17 year old hacks Twitter, then gets hacked

11 April: 17 year old from New York wrote a worm that exploits an XSS vulnerability on Twitter and brought Twitter on it's knees. Sure the worm was mostly harmless, meaning no sensitive information was stolen by the author. Story on xssed.com (including worm code).
16 April: Apparently some hackers didn't like the publicity the worm author has received and hacked into his own system, posting personal and sensitive information (as passwords) here .
On January 2009 a hacker brute forced the site and managed to find an admin password, and thus was able to hijack multiple high profile accounts - more.
liveinspector.gr: το νεο μουσικό site είναι γεγονός!
We interrupt this program to bring you a special announcement: live inspector is up and running!
Ένα μήνα μετά το alpha version, και μετά απο πολλές δοκιμές και διορθώσεις bugs το liveinspector.gr περνάει στη φάση της κανονικής λειτουργίας του!
Πρόκειται για μια προσπάθεια νέων ανθρώπων να φέρει τη ζωντανή μουσική σαν μια βασική διέξοδο έκφρασης. Κάθε συναυλία που έχει προγραμματιστεί για την Ελλάδα και την Κύπρο μπορεί να καταχωρηθεί στο live inspector, είτε απο τους καλλιτέχνες τους ίδιους είτε από οποιονδήποτε, μέσα απο εύχρηστες φόρμες. Οποιοσδήποτε μπορεί επίσης να σχολιάσει μια συναυλία ή έναν καλλιτέχνη, ή να ανεβάσει φωτογραφίες.
Υπάρχουν πολλά περισσότερα χαρακτηριστικά στο live inspector που δεν χρειάζεται να αναφέρω, καθώς ο επισκέπτης μπορεί να τα ανακαλύψει μόνος του. Η ομάδα έχει προσπαθήσει -και ελπίζουμε οτι το καταφέραμε σε μεγάλο βαθμό- να δημιουργήσει ένα λειτουργικό και εύχρηστο site όπου μπορεί κανείς να βρεί εύκολα την πληροφορία που θέλει, μέσα απο μια ευχάριστη πλοήγηση!
Το site είναι φτιαγμένο με django και python, η βάση δεδομένων είναι η mysql, ενώ ο web server είναι -τι άλλο- apache. Η χρήση κάποιου έτοιμου CMS είχε πολύ γρήγορα αποκλειστεί, μιας και θέλαμε να δώσουμε τη δική μας αισθητική και λειτουργικότητα. Το slideshow γίνεται με το φοβερό open source slideshow creator SmoothGallery , ενώ στην αρχική σελίδα υπάρχει ένα flash-άκι που σύντομα θα προβάλει τα posters απο τις συναυλίες της κάθε μέρας!
Επειδή δεν είμαι fan των τεχνολογιών captcha -αυτό που σου προβάλλει μια εικόνα και σου ζητάει να γράψεις τους χαρακτήρες και αναρωτιέσαι γιατί θα έπρεπε να το κάνεις!- έχει γίνει προσπάθεια να περιορίζονται οι επίδοξοι spammers μέσω του memcached, μιας τεχνολογίας που χρησιμοποιείται κυρίως για caching, μπορεί όμως να αποθηκεύει μετρητές comments ή login προσπαθειών χωρίς να επιβαρύνεται έτσι η βάση δεδομένων με επιπλέον queries για καθεμία απο αυτές τις πράξεις! Βέβαια για να κρατήσεις ένα site όσο πιο καθαρό γίνεται απο spam, χρειάζεται συνδυασμός περισσότερων απο μιας λύσεων. Η ενεργή συμμετοχή των χρηστών παίζει ουσιαστικό ρόλο σε αυτή την προσπάθεια. Δίπλα απο κάθε σχόλιο, όπως και από κάθε καλλιτέχνη/συναυλία ή συναυλιακό χώρο υπάρχει η δυνατότητα οποιοσδήποτε χρήστης να ενημερώσει την ομάδα διαχείρισης για την εγκυρότητα του περιεχομένου ή αν πρόκειται για spam. Είμαστε σίγουροι οτι οι χρήστες θα εκτιμήσουν αυτή την δυνατότητα, όπως και εμείς εκτιμούμε τη συνεισφορά τους στο να διατηρηθεί το site καθαρό από spam :)
Θα ήθελα επίσης να αναφέρω οτι υπάρχουν επιπλέον χαρακτηριστικά τα οποία θα προστεθούν στο live inspector με τον καιρό. Enjoy!
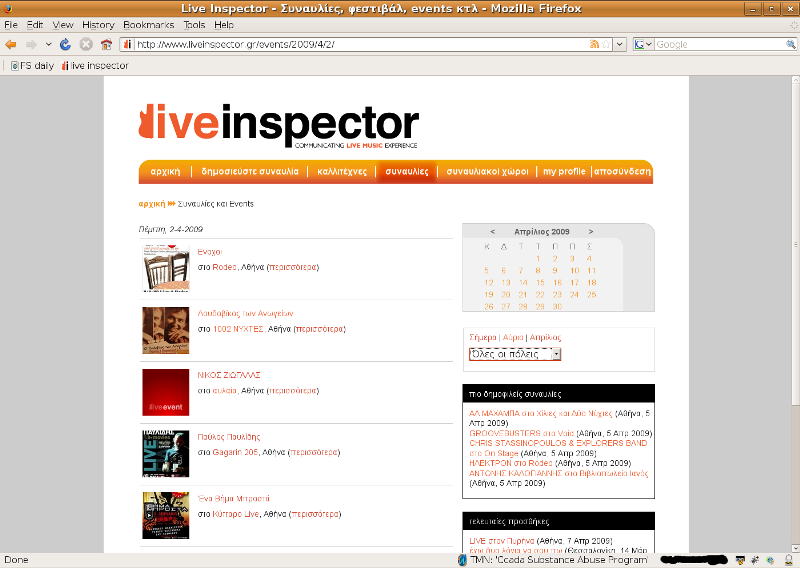
οι συναυλίες μιας μέρας.
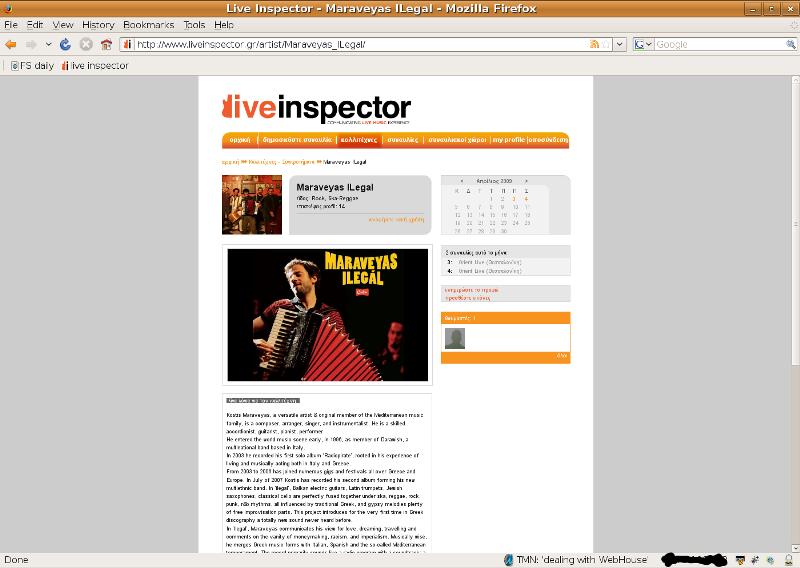
το προφίλ ενός καλλιτέχνη!
Middle East protesters deface US Army and Nato websites
On Thursday 8 Jan, Turkish cracker "Agd_Scorp" defaced the US Army website mdw.army.mil and NATO Parliament www.nato-pa.int, by putting messages in support of the Intifada and protesting against the recent Israeli attacks in Palestine that have resulted in the death of more than 800 of Palestinians so far.
Zone-h has screenshots taken after the defacements here and here.

From
what we can read on zone-h.org, Windows 2003 was the Operating System of
the server hosting the domains, while the attacker
exploited some Sql Injection flaws (on the ASP application powering the websites) for the break-in.
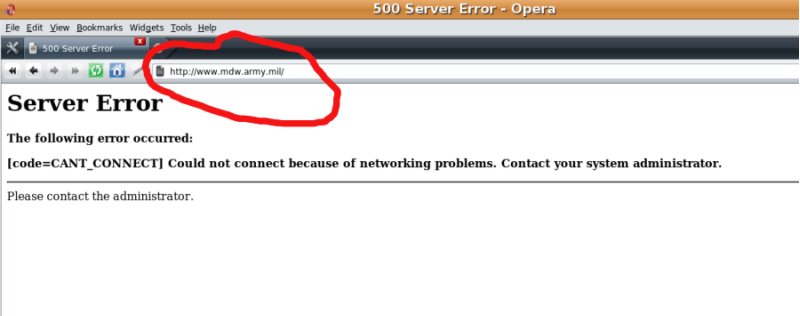
Two days after the incident, mdw.army.mil seems inaccessible, as you can see on the screenshot.
It is interesting what we read on securityfocus for the story. "Last week, several sources reported that thousands of Web sites may
have been defaced by Palestinian sympathizers. Still, this is nothing on the scale of
Georgia or even more recently with the (online) attacks on Kasparov"
25th Chaos Communication Congress - "Nothing to hide"
The Chaos Computer Club (CCC) is a Germany based hacker organization, one of the biggest and most influential. Since its foundation on 1981 they have contributed to the evolution of computer security, freedom of information, development of the hacker ethics and hacker culture!
I have always been fascinated by the diversity of the CCC activities, projects and achievements .
The 25th annual conference organized by the Chaos Computer Club, Chaos Communication Congress took place from 27 to 30 Dec 2008 in Berlin, Germany.
As always, there was a great plethora of lectures and workshops on a multitude of topics, including computer security, hacking, privacy, science, art, society and culture.
For all of us that couldn't make it to Berlin, there are the online proceedings and papers . Not all of the presentations can be found, but one can further search their author's blogs or project pages and make his way.
Several presentations/workshops that I've found extremely interesting so far:
MD5 considered harmful today Highly skilled and motivated team created their own legitimate and trusted Certificate Authority with which they can sign certificates! By exploiting MD5 vulnerabilities, they have made RapidSSL sign a certificate for them whose signature also verifies a CA=YES certificate. They have prooved a vulnerability in the PKI (Public key Infrastructure) that can be used to facilitate MITM (Man-in-the-Middle) attacks against SSL-ed communications. Explained in details in their well written paper on http://www.win.tue.nl/hashclash/rogue-ca/
This paper seems to attract more coverage than any other presented on the conference.
Predictable RNG in the vulnerable Debian OpenSSL package
Security and anonymity vulnerabilities in Tor
Rapid Prototype Your Life Ultra-geek must-read stuff!
Climate Change - State of the Science
We are not blocking traffic, We ARE Traffic
I'm using the Critical Mass slogan for this. Today at 3 in the afternoon a team of students broke into the Biggest Greek TV and media broadcasting channel, NET to protest against the Goebbels style propaganda many channels are following to reverse and revert people's feelings of anger and rage that started on 6 December because of the MURDER of young Alexandros Grigoropoulos by right wing policeman.
The team of young students carried banners saying: "STOP LOOKING, GET OUT ON THE STREETS" and messages of solidarity to youngsters that have been imprisoned in protests for the murder.
Alexis murder as a result of paranoid police brutality has exploded a tremendous wave of anger that has been developed throughout the last decades. No matter what weapons they use (real weapons, like the one that killed the 16 year old child, or less real, like propaganda and disinformation) they can't hide people's anger for the completely incompetent and indescribable governments of the last decades.
Information is the greatest weapon

Hats off to Stelios Kouloglou and his team for the film "Apology of an Economic Hit Man" .
The film is a political thriller based on the novel of John Perkins's , Confessions of an Economic Hit Man (ISBN 0-452-28708-1), featuring the writer himself.
This is a must-see film, that exposes the vicious, sordid, hypocritic and
murderous role of the three letter secret agencies and also
institutions as the World Bank.
The movie has already attained enthusiastic coverage from the global media, including reviews from New York Times , Il Manifesto, Coriere de la Ticino and others.
Watch the trailer


Domain hijacking and other malicious activities with Gmail

A few months ago I read on Gnucitizen about the Gmail CSRF and that was what I think one of the first really big cases of a CSRF attack that became publicly known. Although Google has fixed this issue, it seems there's a new bug somehow similar to that one, and there's some great coverage on the issue at readwriteweb
The story behind this, amongst others contains the story of shocked site owners, getting their domain names hijacked by a malicious group, that asks for a fee (a few 00's dollars) in order to give them their domains back! Nasty.
CSRF is a so called 'Web 2.0 vulnerability', without this meaning that CSRF attacks didn't take place a few years ago. It is an emerging threat, not as well known and understood at the moment, as the different sorts of Injections, like SQL Injection, or Cross Site Scripting, still it is getting a lot of publicity as we hear more and more about high profile incidents .
I'm not going to dive deep into CSRF attacks, as the Wikipedia article explains very well the whole thing. In a few words, "It is a type of malicious exploit of a website whereby unauthorized commands are transmitted from a user that the website trusts." This attack class exploits the trust a site has for a particular user. Since the user is authenticated, any command issued during his sessions is supposed to be valid. So the problem is on the server side, still the user has a problem if a site is vulnerable to CSRF!
a) while logged on to Gmail, a person who owns a domain name and it's contact details are associated to this email address, visits a site that contains malicious code against Gmail
b) since the Gmail user is logged on Gmail, and Gmail is vulnerable to CSRF, the malicious code is executed, that adds a filter on the user's account. Gmail filters are rules to be executed, say for example that each email should be forwarded to address xxx@yyy.com. In this case, a filter is set to forward emails on the malicious guy's email address
c) since paying a close look every now and then on what are your filters isn't very usual (at least for most users, now), it is unlike that the user will notice the difference.
d) during this time, the malicious person collects the user's emails and monitors sensitive information being sent.
He can also use the password reset utilities on the domain registrant, change the password and hijack the domain. 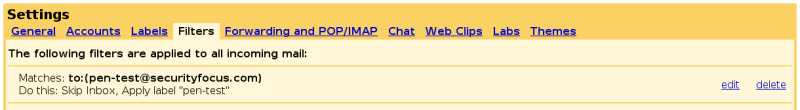
adding filters to Gmail (Settings->Filters->Create a filter)
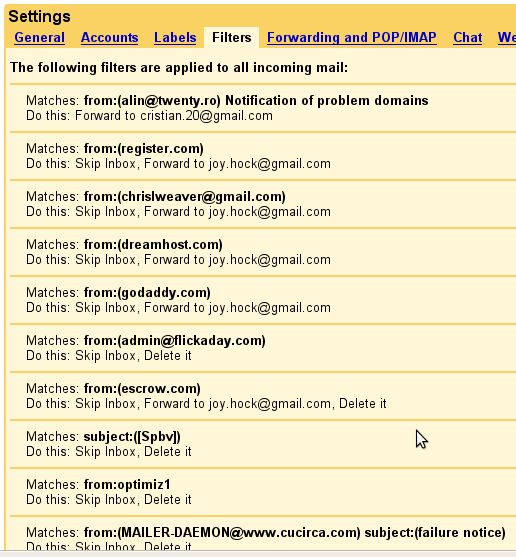
filters of a domain hijack victim, with added filters (image from readwriteweb.com)
Take a moment and think the damage if your email account is compromised. This might result in a far greater loss than physical disasters, eg your hard drive crashing! Not in the case you are a plain user, exchanging mesages with friends and partners, but if your email account is the gateway for online banking systems, paypal, or other systems, or for a domain registrar, as in the scenario we are discussing.
What you can do about that
Google has fixed this vulnerability, however it's good to keep in mind some small things, cause similar scenarios might appear in future.
1) If you use Gmail, check your filters and make sure there's no filters added by others (Settings->Filters)
2) Change your reset passwords/answers. Seriously. Don't allow yourself to get owned because someone reset your password by answering the question 'What's your favorite puppy'. (this also aplies to ALL web based email, like yahoo, hotmail etc).
3) While logged on Gmail, don't visit malicious/questionable sites.
4) Use https://mail.google.com instead of http://mail.google.com (notice the s). Thus all of your session is encrypted (HTTPS), rather than only when you login as it happens with HTTP.
What's really important to remember is in CSRF, or XSS, or other types of attacks, we tend to underestimate the number of web sites/applications that are vulnerable. Also, as users we can't do many things to avoid these attacks (since they are server side), just be informed and suspicious :)
If this sounds interesting to you, check out geekcondition, featuring some great coverage on the issue.
Gnucitizen (what an awesome name!) is an IT security Think Tank, having produced amazing papers and coverage for many issues in the field of IT security. Moreover, the policy they've been following for publicizing vulnerabilities seems very responsive (they even prompt others to inform the vendor for a problem, let the vendor fix it and then publicize it, rather than just publicize it once discovered).
FOSDEM 2009: Free and Open Source Developers' European Meeting

Just received the call for participation for FOSDEM 2009 from one of the organizers. FOSDEM is THE event to visit.
If you're a developer, you'll have the chance to attend some awesome presentations from the people that create major open source programs, such as GNOME, KDE, Firefox, plus meet these people, discuss and exchange opinions!
If you're not a developer, but interested in open source software, trust me after two days in FOSDEM you'll make it your first priority to become a developer, or focus on another activity around open source software (like translations, graphics, system administration, propaganda, obviously coding isn't the only necessary in the open source software ecosystem)!
Finally if you're not interested in open source, and just want to get an idea what it is about, you'll be amazed to see a few thousands of people discussing passionately about it, and you will have the chance to see this software in action, as there is plenty of equipment and the teams behind the software willing to solve all your questions. And what a better way to get introduced to Firefox, or Fedora Linux, or OpenOffice, by talking to these project's communities, that will be there, with plenty of computers for demonstration reasons!
Entrance to
FOSDEM is free of charge and help is provided to newcomers from the big
organizing team, which is populated by volunteers.
I'd dare to
say FOSDEM is one of the ultimate computer related events, not only for
people interested in open source, but also practically everyone that
works with computers or studies computer science. CS university classes should sponsor their students to attend this two days event,
happening every year at Brussels. Also, IT companies could do this,
sponsor people to travel in Brussels for two days to attend the event.
If you are involved on an open source project, maybe you should consider into presenting it at FOSDEM! Lightning talks (15 minute talks) is the correct place for this. Not only your project will get some publicity, you might also attract developers
to join the project, which is something more or less all open source
projects are in continuous need of! And what a better place to
brainstorm about your project, than a place were a few thousands of
developers are hanging around for two days!
If you've heard of
FOSDEM and willing to pay a visit, just do it, this will be worth it
100%. It might be a little early to organize a trip at the moment
(FOSDEM is taking place in Brussels, 7 and 8 February), but if you're
willing to arrange a talk for your project, there are some deadlines,
so better register now.
At http://archive.fosdem.org/2008/ you can find the archives of FOSDEM 2008. Slides, presentations, videos, photos and all material from last year's FOSDEM!